Chapter 17 Exercises
Chapter 17 Exercises
17.1 Binary Codes
Question 17.31
1. Use the circle diagram method shown in Figures 17.1 and 17.2 (page 700) to verify the code words in Table 17.1 (page 702) for the messages 0101, 1011, and 1111.
1.
See Table 17.1 for answer.
Question 17.32
2. Use the circle diagram method to decode the received messages 0111011 and 1000101.
Question 17.33
3. Find the distance between each of the following pairs of words:
- 11011011 and 10100110
- 01110100 and 11101100
3.
(a) 6
(b) 3
Question 17.34
4. Referring to Table 17.1, use the nearest-neighbor method to decode the received words 0000110 and 1110100.
Question 17.35
5. If the code word 0110010 is received as 1001101, how is it decoded using the circle diagram method?
5.
1001101
Question 17.36
6. Suppose that a received word has the circle diagram arrangement shown here:
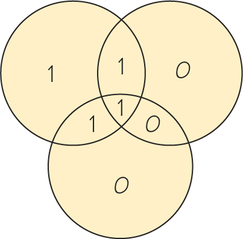
What can we conclude about the received word?
Question 17.37
7. Suppose that a received word has the circle diagram arrangement shown here:
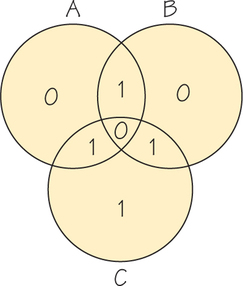
Assuming that exactly one error was made in transmission, what was the sent word?
7.
1101000
Question 17.38
8. If the code word 1010 in the code C2 in Example 4 (page 706) is received as 1000, explain why the error will be detected but cannot be corrected.
Question 17.39
9. For the code C4 in Example 4, decode the following received messages:
- 1101011
- 1011011
- 1100001
9.
(a) 0101011
(b) 1011010
(c) 1110001
Question 17.40
10. If the code word 0010111 in the code C4 in Example 4 is received as 1010110, will the error be detected? Can it be corrected?
17.2 Encoding with Parity-Check Sums
Question 17.41
11. Determine the binary linear code that consists of all possible three-digit messages with three check digits appended using the parity-check sums a2+a3,a1+a3 and a1+a2. (That is, c1=0 if a2+a3 is even, c1=1 if a2+a3 is odd, and similarly for c2 and c3.)
11.
{0000000,0010111, 0101011, 1001101, 1100110,1011010, 0111100, 1110001}
Question 17.42
12. Let C be the code
{0000000, 0010111, 0101011, 1001101, 1100110, 1011010, 0111100, 1110001}
What is the error-correcting capability of C? What is the error-detecting capability of C?
Question 17.43
13. Find all code words for binary messages of length 4 by appending three check digits using the parity-check sums a2+a3+a4,a2+a4, and a1+a2+a3. Will this code correct any single error?
13.
0000000, 1000001, 0100111, 0010101, 0001110, 1100110, 1010100, 1001111, 0110010, 0101001, 0011011, 1110011, 1101000, 1011010, 0111100, 1111101. No, because 1000001 has weight 2.
Question 17.44
14. Consider the binary linear code
C=000000,100110,010101,001011,110011,101101,011110,111000
Use nearest-neighbor decoding to decode 101100 and 101011. If a received word is 001100, can you determine the intended code word? Explain your reasoning.
Question 17.45
15. Construct a binary linear code using all eight possible binary messages of length 3 and appending three check digits using the parity-check sums a1+a2, a2+a3 and a1+a3. Decode each of the received words below by the nearest-neighbor method:
001001, 011000, 000110, 100001
15.
000000, 100101, 010110, 001011, 110011, 101110, 011101, 111000. 001001 is decoded as 001011; 011000 is decoded as 111000; 000110 is decoded as 010110; 100001 is decoded as 100101.
Question 17.46
16. Extend the code words listed in Table 17.1 (page 702) to eight digits by appending a 0 to words of even weight and a 1 to words of odd weight. What are the error-detecting and error-correcting capabilities of the new code?
Question 17.47
17. Extend the code words listed in Table 17.2 (page 704) to eight digits by appending a 0 to words of even weight and a 1 to words of odd weight. What are the error-detecting and error-correcting capabilities of the new code?
17.
00000000, 00010111, 00101110, 01001011, 10001101, 11000110, 10100011, 10011010, 01100101, 01011100, 00111001, 11101000, 11010001, 10110100, 01110010, 11111111. The code will detect any three errors or correct any single error.
Question 17.48
18. Suppose that the weight of a binary linear code is 6. How many errors can the code correct? How many errors can the code detect?
Question 17.49
19. How many code words are there in a binary linear code that has all possible messages of length 5 with three check digits appended? How many possible received words are there with this code?
19.
25=32;28=256.
17.3 Data Compression
Question 17.50
20. Suppose we code a four-symbol genetic set {A, C, T, G} into binary form as follows:
A→0C→10T→110G→111
Convert the sequence ACAAGTAAC into binary code.
Question 17.51
21. Use the code in Exercise 20 to determine the sequence of symbols represented by the binary code 001100001111000.
21.
AATAAAGCAA
Question 17.52
22. Suppose that we code a five-symbol set {A, B, C, D, E} into binary form as follows:
A→0B→10C→110D→1110E→1111
Convert the sequence of AEAADBAABCB into binary code. Determine the sequence of symbols represented by the binary code 01000110100011111110.
Question 17.53
23. Use the code in Exercise 22 to convert the sequence EABAADABB into binary code. Determine the sequence of letters represented by the binary code 001000110011110111010.
23.
111101000111001010; AABAACAEADB
Question 17.54
![]() 24. Devise a variable-length binary coding scheme for a six-symbol set {A, B, C, D, E, F}. Assume that A is the most frequently occurring symbol, B is the second most frequently occurring symbol, and so on.
24. Devise a variable-length binary coding scheme for a six-symbol set {A, B, C, D, E, F}. Assume that A is the most frequently occurring symbol, B is the second most frequently occurring symbol, and so on.
Question 17.55
25. Judging from the frequency table in Figure 17.9 (page 709), what are the three most frequently occurring consonants in English text material? What is the most frequently occurring vowel?
25.
T, N, and R; E
Question 17.56
26. Explain why Morse code must include a space after each letter, but fixed-length codes do not.
Question 17.57
27. Following are the closing values (rounded to the nearest integer) of the Dow Jones Industrial Average stock market values for a two-week period. Use the delta function method to compress these values. What percentage reduction in characters is there?
13403137391381613767138201375913779138781391313896
27.
13403 336 77 −49 53 −61 20 99 35 −17; we go from 59 characters to 36 characters, a reduction of almost 39%.
Question 17.58
28. The following numbers were encoded using delta function encoding. Determine the original numbers.
1207373−57−97−234−105178−7327579−183−146−94129
Question 17.59
29. Assume that a dataset of four letters occurs with the following probabilities:
A0.425B0.210C0.215D0.150
Use a Huffman tree to create a Huffman code for A, B, C, and D.
29.
A is 0; B is 111; C is 10; D is 110.
Question 17.60
30. Given that the delta function was used to create values in the following list
13403 336 77 −49 53 −61 20 99 35 −17
recreate the original list.
Question 17.61
31. Decode the binary string
11100100001001110110011010
which has been encoded using the Huffman code given on page 713.
31.
BCEEFCDDCFF
Question 17.62
32. Use a Huffman tree to assign a binary code to the letters that occur with the following probabilities:
A0.025B0.150C0.015D0.170E0.200E0.225G0.215
17.4 Cryptography
Question 17.63
33. Use hand computations to calculate the following.
- 80 mod 26
- −42 mod 26
- 269 mod 26
33.
(a) 2
(b) 10
(c) 9
Question 17.64
34. Solve for x by trial and error.
- 3x mod
Question 17.65
35. Use the Caesar cipher to encrypt the message RETREAT. Decrypt the message DGYDQFH, which was encrypted using the Caesar cipher.
35.
UHWUHDW; ADVANCE
Question 17.66
36. Suppose a message encrypted with a Caesar shift can be decoded with the same shift. What is the shift?
Question 17.67
37. Using to label the positions of the letters , suppose that we create a cipher by replacing the letter in position with the letter in position . How many iterations of this cipher must be done before a message will return to its original state?
37.
13
Question 17.68
38. The message ADDAOS was encrypted using the decimation cipher with the key 7. Decrypt it.
Question 17.69
39. Explain why 2 cannot be used as the key in a decimation cipher.
39.
There is no integer such that modulo 26.
Question 17.70
40. If you attempted to use the decimation cipher with the key 13, how would the word MESSAGE be encrypted?
Question 17.71
41. Use the decimation cipher with the key 5 to encrypt RETREAT.
41.
HURHUAR
Question 17.72
42. Suppose you wanted to break a code that employed a linear cipher by trying all possible linear ciphers. How many would you have to test to try every one?
Question 17.73
43. Find a formula for a linear cipher that decrypts messages encrypted using the formula .
43.
Question 17.74
44. List all possible permutations of 1, 2, 3, including 1,2, 3 itself, in a systematic way. (The original ordering 1,2, 3 is viewed as a permutation to simplify various theoretical arguments.)
Question 17.75
45. Encrypt the message ADVANCE WHEN READY using the permutation .
45.
VAADENWCNHREDEYA
Question 17.76
46. Encrypt the message ATTACK POSTPONED using the permutation .
Question 17.77
47. The message EMTENAOTXOQN was encrypted using the permutation . Decrypt it.
47.
MEET AT NOON
Question 17.78
48. The message TAACTPKSTOOPEDN was decrypted using the permutation . Decrypt it.
Question 17.79
49. How many permutations of 1, 2, 3, 4 are possible, including the original ordering 1, 2, 3, 4?
49.
Question 17.80
50. Use the Playfair cipher with the keyword IMAGINE to encrypt the plaintext CALL ME.
Question 17.81
51. The ciphertext WR VI SE CW RY was encrypted with the Playfair cipher using the key WORLD WAR II. Decipher it.
51.
DO NOT CALL
Question 17.82
52. Explain why the ciphertext BT TZ PM UO AW AC HK EU W cannot have been encoded using the Playfair cipher.
Question 17.83
53. How many possible keys are there for a Jefferson wheel with six disks?
53.
Question 17.84
54. Referring to the Jefferson wheel with six disks and the key shown in Example 20 (page 725), what would the encrypted message be if we used the row that is just above the row ATTACK?
Question 17.85
55. Referring to the Jefferson wheel with six disks and the key shown in Example 20, what row was used to create the encrypted message MCEMPL?
55.
Third above the row ATTACK
Question 17.86
56. Referring to the Jefferson wheel with six disks shown in Example 20 and the key 5, 1, 4, 2, 6, 3, encrypt the message DEPLOY, using the row directly below the message.
Question 17.87
57. Given that BEATLES was used as the keyword for the Vigenère cipher to encrypt SSLETRY TXOGPW, decrypt the message.
57.
ROLLING STONES
Question 17.88
58. Use the Vigenère cipher with the keyword CLUE to encrypt the message THE WALRUS WAS PAUL.
Question 17.89
59. Use the Vigenère cipher with the keyword HELP to encrypt the message PHONE HOME.
59.
WLZCL LZBL
Question 17.90
60. Use the linear cipher method with and to encrypt GOOD.
Question 17.91
61. Given that the received message ZVW was encrypted using the linear cipher method with and , decrypt the message.
61.
SUN
Question 17.92
62. Add the following pairs of binary strings.
- 10111011 and 01111011
- 11101000 and 01110001
Question 17.93
63. For any two binary strings and of the same length, define to be the string obtained by summing the strings as explained in Example 21 (page 726). Find for each of the following cases.
63.
(a) 1111101
(b) 1100011
Question 17.94
64. Suppose that and are two binary words of length 7 whose distance apart is 7. What string is ?
Question 17.95
65. Given the binary word , find all binary words of length 7 that are a distance of 1 from .
65.
0010110, 1110110, 1000110, 1011110, 1010010, 1010100, 1010111
Question 17.96
66. Suppose that and are binary code words of the same length. Using the method of summing binary strings as shown in Example 21, explain why the distance from to is the same as the weight of .
Question 17.97
67. Suppose that , , and are binary code words of the same length. Using the method of summing binary strings as shown in Example 21, explain why the distance from to is the same as the distance from to .
67.
Recall that the distance between two strings is the number of positions by which they differ. Observe that everywhere and agree, so do . Conversely, in every position that and disagree, so do .
Question 17.98
68. All binary linear codes have the property that the sum of two code words is another code word. Use this fact to determine which of the following sets cannot be a binary linear code.
Chapter Review
Question 17.99
69. Messages encrypted with the __________ cipher are the hardest to break.
- Vigenère
- decimation
- linear
69.
a
Question 17.100
70. Explain why for any choice of the key shown in Table 17.4 (page 717) the number 13 is always encrypted as 13.
Question 17.101
71. Suppose a Huffman tree has been used to create a binary code for the letters through , and the results include , , and . If the code has only two code words of length 6 and one of length 5, what can you say about the probability of the occurrence of the letters , , and ?
71.
is the least likley, is the second least likely, and is the third least likley.
Question 17.102
72. What is the minimum weight of a binary code that can correct any 3 or fewer errors?
Question 17.103
73. Explain why encoding ID numbers by multiplying them by 15 would not detect the single-digit error of replacing 1328 by 1326.
73.
The difference is a multiple of 15.
Question 17.104
74. Explain why any error involving the code word 001 in the code in Example 4 (page 706) is not detected.