Background Texts
Included here are statistics on bandwidth use from the campus IT office, an e-
Download the Campus Acceptable Use Policy.
Download the Statistics on Bandwidth Usage.
Statistics on Bandwidth Use from the Campus IT Office
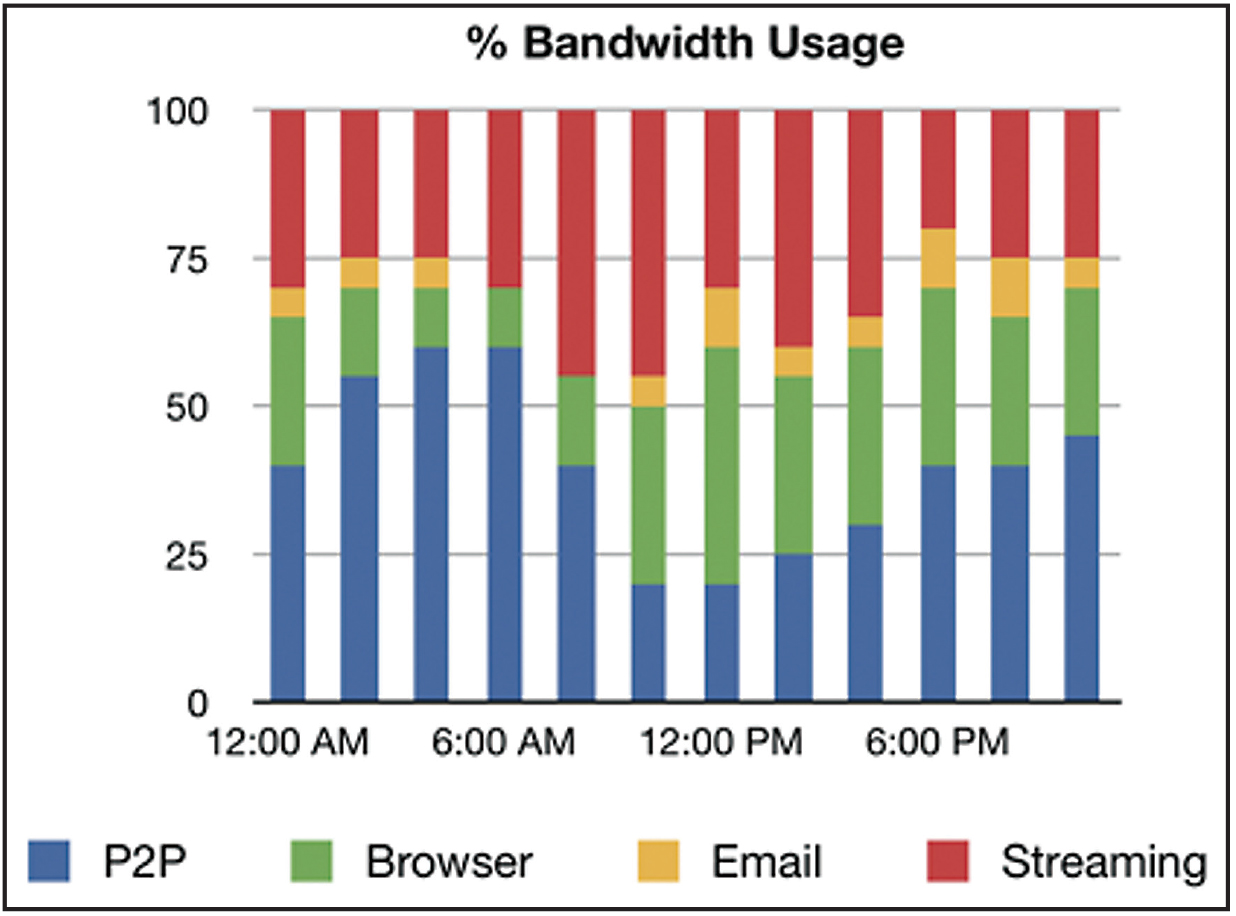
| P2P | Browser | Streaming | ||
| 12:00 AM | 40 | 25 | 5 | 30 |
| 2:00 AM | 55 | 15 | 5 | 25 |
| 4:00 AM | 60 | 10 | 5 | 25 |
| 6:00 AM | 60 | 10 | 0 | 30 |
| 8:00 AM | 40 | 15 | 0 | 45 |
| 10:00 AM | 20 | 30 | 5 | 45 |
| 12:00 PM | 20 | 40 | 10 | 30 |
| 2:00 PM | 25 | 30 | 5 | 40 |
| 4:00 PM | 30 | 30 | 5 | 35 |
| 6:00 PM | 40 | 30 | 10 | 20 |
| 8:00 PM | 40 | 25 | 10 | 25 |
| 10:00 PM | 45 | 25 | 5 | 25 |
• Numbers in the table represent the percentage of network resources that were devoted to different categories of applications during a typical 24-
The Campus’s Current Acceptable Use Policy
Acceptable Use Guidelines for Computer and Network Facilities
The University strives to provide fair and distributed access to information technology (i.e., computer and network) facilities for a large number of users. The acceptable use guidelines that follow apply equally to all types of electronic information services, including electronic mail (e-
- WMU supports the principles of academic freedom and free inquiry and expression in the online environment as well as in the classroom. This freedom must be balanced, however, with the responsibility not to infringe on other individuals’ rights.
- Acceptable use of shared information technology facilities follows the same standards of common sense, courtesy, and restraint that govern the use of other public facilities. WMU regulations VIII K Sexual Harassment Policy and VIII Q Cultural Diversity Policy also apply to the online environment. Acceptable use requires users to be ethical and respectful of the rights of others and of the diversity of the University community, and to maintain a climate that does not interfere with the studies, work, or living environment of any members of the WMU community.
- Acceptable use of information facilities respects individuals’ rights to privacy and to freedom from threats, intimidation, harassment, and unwarranted annoyance.
- Acceptable use includes the right of individuals to access and save any legal files on the Internet. It is not acceptable to display and print potentially offensive material in public computer labs where others cannot avoid seeing these files. Such material should be viewed in a private location. Material that is potentially offensive to others should not be publicly displayed without an academic reason.
- Acceptable 6use standards require everyone to take prudent and reasonable steps to prevent unauthorized access. Access authorization relies on user identification and password for each user. The user ID forms the basis for mechanisms that are designed to establish ownership and responsibility for computing resources and use. Acceptable use respects these identification and security mechanisms.
- Acceptable use requires that all users refrain from any illegal and improper intrusions into the accounts of others and/or into any University information technology resources and systems.
- Acceptable use requires that all users recognize and honor the intellectual property rights of others.
- Acceptable use of information facilities respects University regulations, contracts with University suppliers, and all local, state, and federal laws. Software theft, also known as software piracy, is a topic of much concern. Acceptable use of software respects all associated license and/or purchase agreements; if you have not met the conditions of such an agreement for a given software package, do not copy the package for your use.
- Acceptable use of all off-
campus network connections (i.e., use of the Internet) respects the University’s network access contracts that impose strict requirements. In general, off- campus network use must be for education or research. The University’s access contracts prohibit commercial activities such as advertising. They also require all users to promote efficient use of the network to minimize and avoid, if possible, congestion of the network that interferes with the work of others. - Acceptable use of information technology resources requires that all users refrain from acts that waste resources and prevent others from having broad access to University computers and resources.
Enforcement
When instances of unacceptable use come to its attention, the University will investigate them and may take action to prevent their further occurrence. During an investigation, the University reserves the right to copy and examine any files or information residing on University systems allegedly related to improper use, including the contents of electronic mailboxes. Investigations that discover improper use may cause the University’s authorized investigators to
- limit the access of those found using facilities or services improperly;
- disclose information found during the investigation to other University authorities;
- begin discipline actions as prescribed by University policies and procedures;
- install automatic measures to limit improper use.
E-mail from the University President to Your Committee
| To: | Ad Hoc File- |
| From: | Adrian Wu <president@wmu.edu> |
| Date: | January 12, 2014 |
| Subject: | Initial Committee Meeting and Charge |
I wanted to thank each of you for agreeing to serve on the Ad Hoc File-
In disciplinary meetings with students, faculty, and staff about these issues, I often find that individuals do not realize the impact, both technical and legal, of their activities. In retrospect, it appears that our existing policy, while legally sound, is far too vague and dense. As I mentioned earlier, I’ve asked your committee to create a shorter, clearer file-
In discussions with the University’s IT staff, faculty, students, and legal counsel, I have determined that the file-
Ethical Issues: As an educational institution, we place high value on supporting the development of ethical citizens. Because much file-
sharing activity (perhaps the majority) involves the theft of intellectual property, the University’s file- sharing policy should emphasize an ethical approach to the use of campus resources and intellectual property in general. Legal Issues: Entwined with the ethical aspects are the legal consequences of illegal file sharing, both for individual users and for the University. Over the last few years, several high-
profile legal cases have been instituted against individuals accused of file sharing. Although such cases have not yet been brought against any of our students, the University has received a number of cease- and- desist orders and related legal warnings from the legal representatives of several large media companies. So far, we have dealt with these occurrences on an informal basis. However, the University legal counsel suggests that the chance of formal legal action remains a major concern. 9In addition, the warnings the University has received invariably include threatening language about the University’s liability if the University cannot show that it is taking a strong stance to prevent illegal file sharing. We believe that the Digital Millennium Copyright Act absolves the University of liability. But the costs of defending our position would itself be onerous and should be avoided if at all possible.
Functional Issues: Over the last year, bandwidth on the University network has become increasingly strained. Conversations with our IT Department indicate that a significant amount of load is due to students sharing large files, typically copyrighted movies and software. Such use, in addition to being both unethical and illegal, also impacts the legitimate educational use of the campus network by students and faculty. In isolated (but increasingly frequent) instances, students and faculty have been unable to access large datasets, student-
produced videos from class sites, and (in one case) the University’s service of providing streaming video of live coverage of our basketball team during a championship playoff (a situation that angered many supporters in our local community as well as University alumni). Educational Issues: We are, first and foremost, an educational institution. I strongly believe that many of the issues involved in illegal file sharing would be resolved by educating students and faculty about the ethical, legal, and functional aspects involved. The e-
mail message that I’ve asked you to send to the campus community should ultimately be an educational document.
My sincere thanks again for your future efforts on the activities of the committee, and I look forward to reading the results.
Sincerely,
Adrian Wu
President, WMU