Using Social Media and Other Electronic Tools in Collaboration
The tremendous growth in the use of social-
With each passing year, more professionals are using social media in the workplace. A 2012 survey by the human-
Professionals use many types of electronic tools to exchange information and ideas as they collaborate. The following discussion highlights the major technologies that enable collaboration: word-
WORD-
Most word processors offer three powerful features that you will find useful in collaborative work:
The comment feature lets readers add electronic comments to a file.
The revision feature lets readers mark up a text by deleting, revising, and adding words and indicates who made which suggested changes.
The highlighting feature lets readers use one of about a dozen “highlighting pens” to call the writer’s attention to a particular passage.
MESSAGING TECHNOLOGIES
Two messaging technologies have been around for decades: instant messaging and email. Instant messaging (IM) is real-
In the last decade, several new messaging technologies have been introduced that are well-
For more about writing emails, see “Writing Emails” in Ch. 9.
Text messaging enables people to use mobile devices to send messages that can include text, audio, images, and video. Texting is the fastest-
Microblogging is a way of sending very brief textual messages to your personal network. You might use the world’s most popular microblog, Twitter, which now has more than half a billion users. Although some organizations use Twitter, many use Twitter-
VIDEOCONFERENCING
Videoconferencing technology allows two or more people at different locations to simultaneously see and hear one another as well as exchange documents, share data on computer displays, and use electronic whiteboards. Systems such as Skype are simple and inexpensive, requiring only a webcam and some free software. However, there are also large, dedicated systems that require extensive electronics, including cameras, servers, and a fiber-
Participating in a Videoconference

Follow these six suggestions for participating effectively in a videoconference.
Practice using the technology. For many people, being on camera is uncomfortable, especially the first time. Before participating in a high-
stakes videoconference, become accustomed to the camera by participating in a few informal videoconferences. Arrange for tech support at each site. Participants can quickly become impatient or lose interest when someone is fumbling to make the technology work. Each site should have a person who can set up the equipment and troubleshoot if problems arise.
- Page 45
Organize the room to encourage participation. If there is more than one person at the site, arrange the chairs so that they face the monitor and camera. Each person should be near a microphone. Before beginning the conference, check that each location has adequate audio and video as well as access to other relevant technology such as computer monitors. Finally, remember to introduce everyone in the room, even those off camera, to everyone participating in the conference.
Make eye contact with the camera. Eye contact is an important element of establishing your professional persona. The physical setup of some videoconferencing systems means you will likely spend most of your time looking at your monitor and not directly into the camera. However, this might give your viewers the impression that you are avoiding eye contact. Make a conscious effort periodically to look directly into the camera when speaking.
Dress as you would for a face-
to- Wearing inappropriate clothing can distract participants and damage your credibility.face meeting. Minimize distracting noises and movements. Sensitive microphones can magnify the sound of shuffling papers, fingers tapping on tables, and whispering. Likewise, depending on your position in the picture frame, excessive movements can be distracting.
WIKIS AND SHARED DOCUMENT WORKSPACES
Ten years ago, people would collaborate on a document by using email to send it from one person to another. One person would write or assemble the document and then send it to another person, who would revise it and send it along to the next person, and so forth. Although the process was effective, it was inefficient: only one person could work on the document at any given moment. Today, two new technologies—
A wiki is a web-
A shared document workspace makes it convenient for a team of users to edit a file, such as a Prezi or PowerPoint slide set or a Word document. A shared document workspace such as Microsoft SharePoint or Google Drive archives all the revisions made by each of the team members, so that the team can create a single document that incorporates selected revisions. Some shared document workspaces enable a user to download the document, revise it on his or her computer, and then upload it again. This feature is extremely convenient because the user does not need to be connected to the Internet to work on the document.
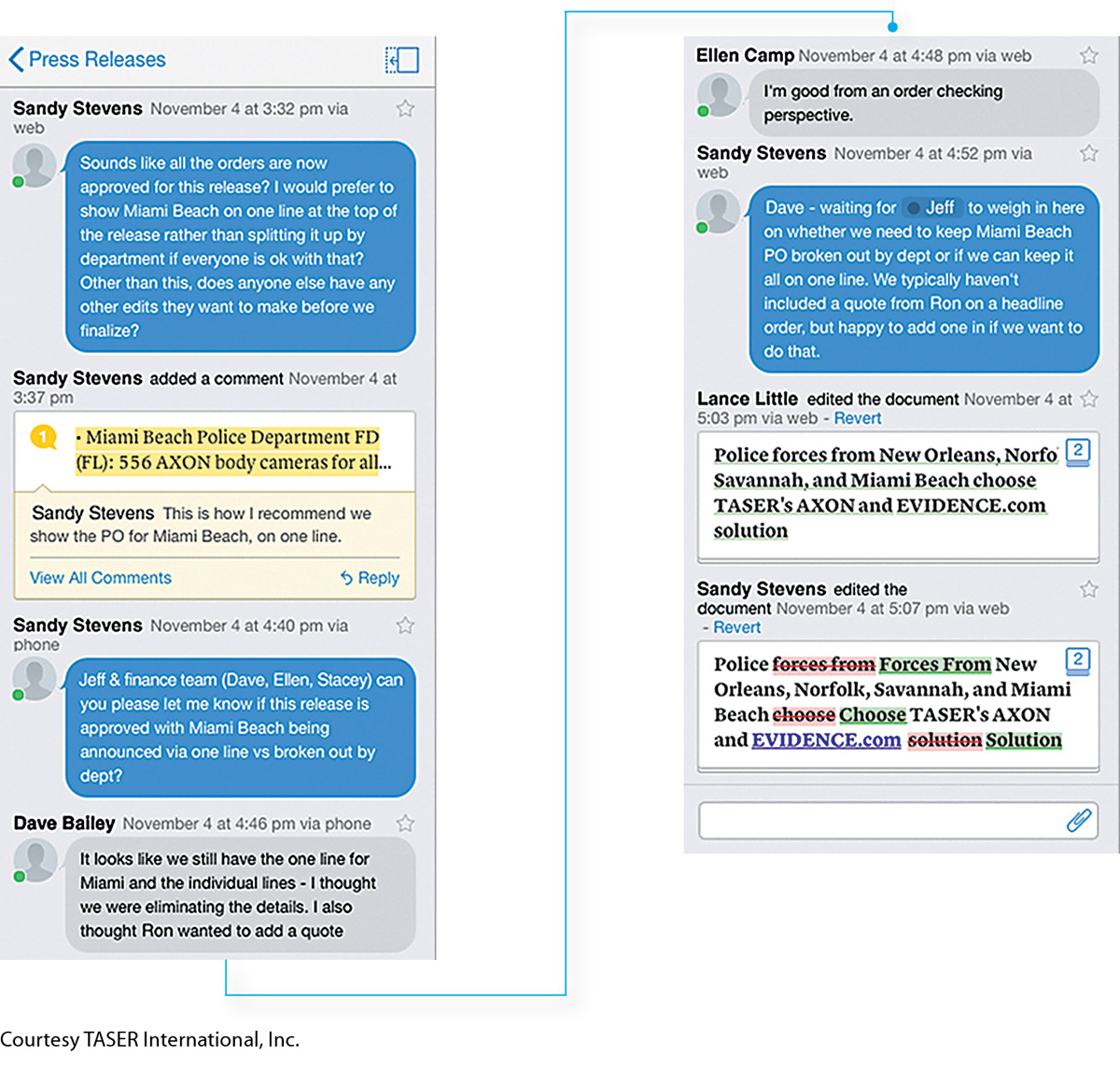
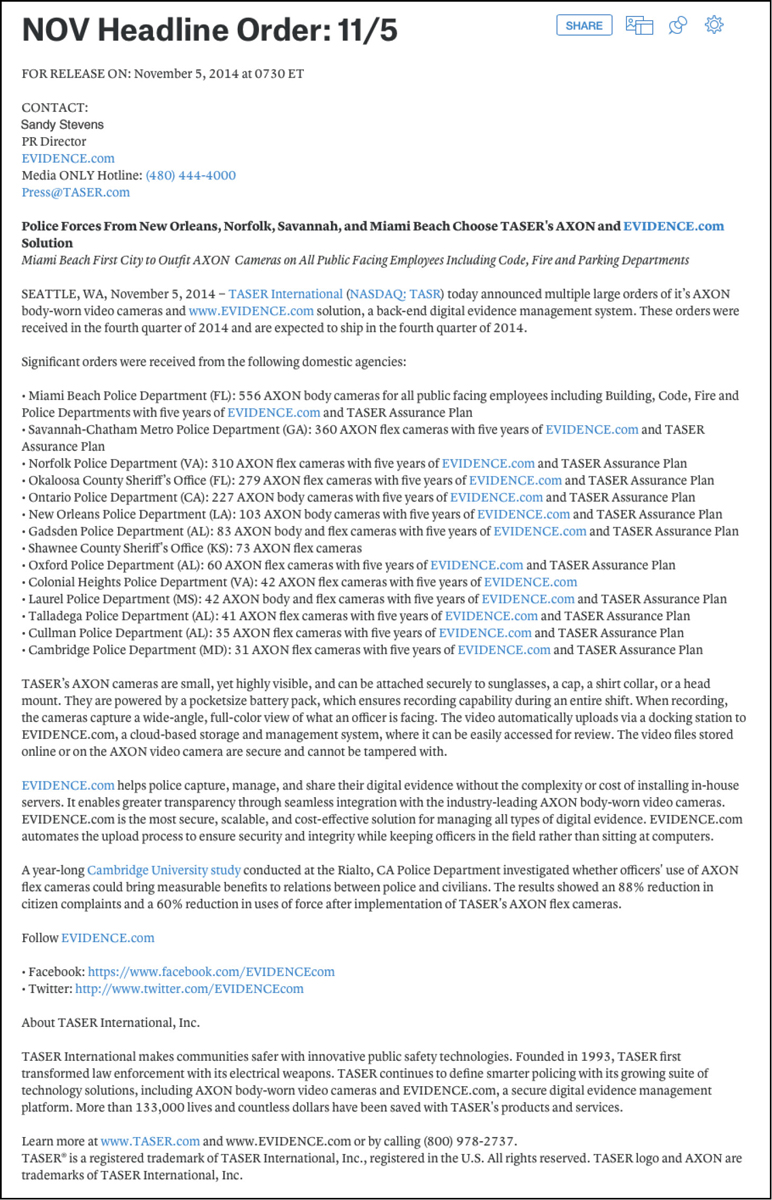
TASER, a company that manufactures law-
TASER’s press releases are developed by many teams, including some from outside the company. Before using Quip, Siegmeth’s team had to consolidate edits made to various versions of the document by other teams and make sure all the contributors received updates about the progress of the press release. Quip’s chat thread streamlines all communication regarding the document in a single place, ensuring that all parties are kept in the loop. TASER has also found that Quip motivates employees to make their contributions more quickly than they did when working with email and a word processor. “I’ve found that once someone goes in to make an edit or a comment, others will jump in there too and offer their approval or other edits,” Siegmeth says.
ETHICS NOTE
MAINTAINING A PROFESSIONAL PRESENCE ONLINE
For more about maintaining a professional presence online, see “Understanding Ethical and Legal Issues Related to Social Media” in Ch. 2.
According to a report from Cisco Systems (2010), half of the surveyed employees claim to routinely ignore company guidelines that prohibit the use of social media for non-
Although the law has not always kept pace with recent technological innovations, a few things are clear. You and your organization can be held liable if you make defamatory statements (statements that are untrue and damaging) about people or organizations, publish private information (such as trade secrets) or something that publicly places an individual “in a false light,” publish personnel information, harass others, or participate in criminal activity.
In addition, follow these guidelines to avoid important ethical pitfalls:
Don’t waste company time using social media for nonbusiness purposes. You owe your employer diligence (hard work).
Don’t divulge secure information, such as a login and password that expose your organization to unauthorized access, and don’t reveal information about products that have not yet been released.
Don’t divulge private information about anyone. Private information relates to such issues as religion, politics, and sexual orientation.
Don’t make racist or sexist comments or post pictures of people drinking.
If your organization has a written policy on the use of social media, study it carefully. Ask questions if anything in it is unclear. If the policy is incomplete, work to make it complete. If there is no policy, work to create one.
For an excellent discussion of legal and ethical aspects of using your organization’s social media, see Kaupins and Park (2010).
Although this section has discussed various collaboration tools as separate technologies, software companies are bundling programs in commercial products such as IBM Sametime, Adobe Creative Cloud, and Microsoft Lync, which are suites of voice, data, and video services. These services usually share four characteristics:
They are cloud based. That is, organizations lease the services and access them over the Internet. They do not have to acquire and maintain special hardware. This model is sometimes called software as a service.
They are integrated across desktop and mobile devices. Because employees can access these services from their desktops or mobile devices, they are free to collaborate in real time even if they are not at their desks. Some services provide presence awareness, the ability to determine a person’s online status, availability, and geographic location.
- Page 49
They are customizable. Organizations can choose whichever services they wish and then customize the services to work effectively with the rest of their electronic infrastructure, such as computer software and telephone systems.
They are secure. Organizations store the software behind a firewall, providing security: only authorized employees have access to the services.